It is always a concern of users to surf the internet in privacy. However, surfing on the usual operating systems can’t provide the security you want. There’s no need to worry, Linux is among the most private operating systems available. So in this blog, we will list the best Linux Distros for Privacy.
Best Linux Distros for Privacy – 2022
The below list is completely based on the user reviews, features, security, privacy, and accessibility of these Linux distros.
1. Qubes OS
Qubes OS is a single-user operating system based on open-source, independent software. Providing security through isolation is one of the main objectives of Qubes OS (security-focused desktop operating system).
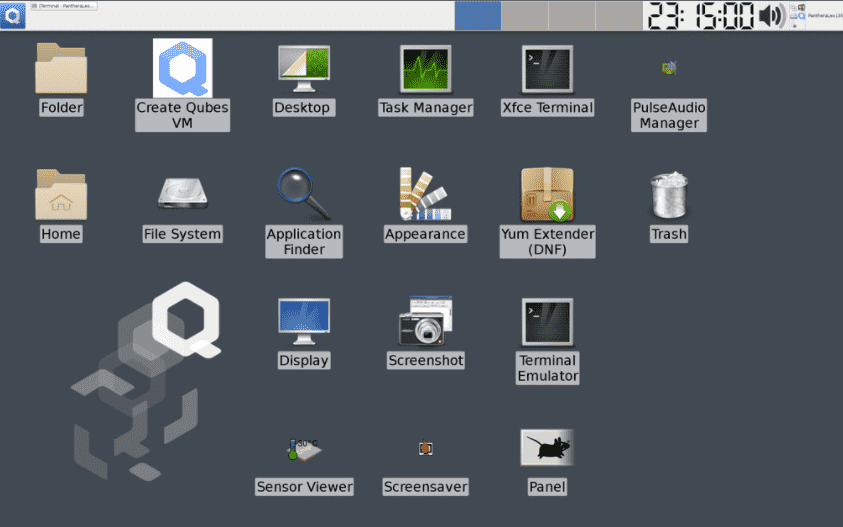
In Qubes, We can separate hardware controllers into functional domains (e.g., USB controller domains, network domains). In contrast, domains with different levels of trust can decide the user’s digital life, and there are two main dimensions of Qubes OS isolation. In this way, we can run each domain separately in a virtual machine.
By default, Qubes is not a multiuser system, and this virtual machine has passwordless root access, i.e., passwordless sudo. Though UEFI Secure Boot isn’t supported, it isn’t considered a major security risk.
Features of Qubes OS
- Through advanced virtualization techniques on other physical machines, different pieces of software are provided with strong isolation.
- The template system allows users to share root files without sacrificing security.
- Qubes OS is free to modify, copy, and use.
- Qubes U2F Proxy allows us to use its two-factor authentication tools without exposing the web browser to the entire USB stack.
- For private key storage, split GPG is used.
- The isolation of USB controllers and network cards provides secure device handling.
2. Tails – Incognito Linux system
The Amnesic Incognito Live System, i.e., Tails, is a type of operating system that protects our system from censorship and surveillance. Tails is a security-focused Debian-based Linux distribution whose primary purpose is to maintain anonymity and privacy. Through Tor, we can block any non-anonymous connection and force all its outgoing and incoming connections to go. This operating system is designed to work as a Live USB or Live DVD. No digital footprint will be left on the machine unless explicitly asked to leave a footprint.

Tails provide several applications for communicating securely and working with sensitive documents. You can also run it as a virtual machine with some added security risks. Tails come with UEFI Secure Boot. Tails distro depends on the underlying operating system to provide the level of security that individual users cannot achieve. To continue serving the Linux community and remain independent, Tails Project relies heavily on donations and participation.
Features of Tails
- Tails use the tor network to avoid censorship and protect our online privacy.
- Tails do not leave any trace when the computer is shut down.
- Tails have some default settings that are safe and ready to use.
- With Tails distro, users can perform secure cryptocurrency transactions with a built-in bitcoin wallet.
- Tails include the Aircrack-NG wireless auditing tool.
3. Whonix Linux for Security
Whonix is software designed to create anonymity and privacy by helping users run applications anonymously. You can run Whonix on the Debian Linux system, which uses two virtual machines such as the Tor “gateway” and the “Workstation.” It is currently working on a unified desktop environment.
Whonix sincerely appreciates contributions and donations to support the project’s ongoing efforts and encourages users to provide feedback on their experiences.
Features of Whonix
- Whonix users can install LKRG, or Linux Kernel Runtime Guard, as a kernel module. This module performs runtime integrity checks of the Linux kernel to detect exploits and security vulnerabilities.
- Mozilla Thunderbird PGP email comes pre-installed on this distro.
- The OS chooses a guest/innovative host to prevent DNS, IP leaks and hide identities behind anonymous proxies of users.
- Whonix ensures complete instant messaging and anonymous web browsing through Tox’s instant messenger and Tor browser application.
4. Kali Linux
Kali Linux has a wide range of utilities and tools for penetration testing. Security researchers, ethical hackers, and pentesters around the world rely on this distro for its many tools. From information gathering to final reporting, Kali Linux allows IT professionals and security professionals to assess the security of their systems.
This distro is named after the Hindu goddess “Kali”. Users can run it on ARM devices like Raspberry Pi. Kali Linux’s training suite is available on its website under the name Dojo.

Features of Kali Linux
- All the training-related resources of Kali Linux are available on its website for free.
- The “forensic” mode of this distro makes it perfect for forensic work.
- Users can customize and automate Kali Linux installation on their network.
- Kali Linux with live-builds provides flexibility by providing complete customization.
- Kali Linux protects sensitive painting data against theft, tampering, loss, etc., with LUKS full-disk encryption.
5. Linux Kodachi for Privacy
Linux Kodachi is an operating system based on Ubuntu 18.04.6. It considers all those features of the users where the person concerned needs privacy to be safe. For this, it provides an anonymous, anti-forensic, and secure operating system. Linux Kodachi can be run from a USB thumb drive or DVD, which is a Debian-based distribution.
Distribution obscures the user’s network location and filters all network traffic through Tor and VPNs. Kodachi tries to clean itself by removing traces of its use. Kodachi is a live operating system that we can start on almost any computer from SD card, USB, or DVD stick.
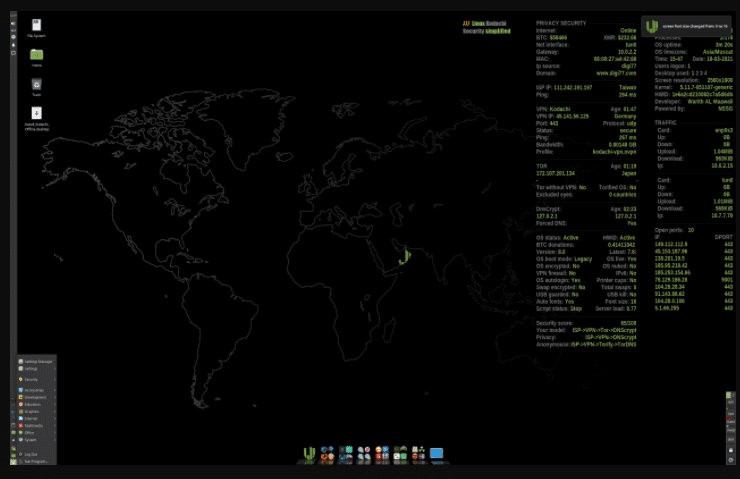
Features of Linux Kodachi
- Privacy and use of state-of-the-art cryptographic tools; to encrypt instant messaging, email, and files.
- There is no trace on the system until the users explicitly ask for it.
- It would be best to go through the VPN and then the Tor network with DNS encryption whenever you connect to the Internet.
- Users can use the Internet anonymously without making a footprint on the web.
6. BlackArch Linux- Security Testing
BlackArch Linux is a penetration testing distribution based on Arch Linux. It has 2743 tools in its repository that users can install in groups or individually. Moreover, BlackArch Linux can be installed alongside existing Arch installations.
Once fully installed, BlackArch is similar in use to both Kali Linux and Parrot OS. BlackArch does not provide a desktop environment like other distributions, but many do provide pre-configured window managers. BlackArch Linux can be run as a live system similar to Parrot and Kali and burned to an ISO image. BlackArch can be installed on any existing Arch installation as an unofficial user repository.

Features of BlackArch Linux
- The modular package feature allows users to install tools in groups or individually.
- The distro provides the ability to build an installer from the source.
- BlackArch Linux comes with a variety of preconfigured window managers.
- It supports various architectures and more than 1800 tools.
7. Parrot OS – for Security experts
A worldwide community of security experts and developers, Parrot OS aims to make their jobs more reliable, standardized, and accessible by building a shared framework of tools. With Parrot OS, multiple cyber security operations can be conducted, from reverse engineering to painting and digital forensics.
Parrot OS provides users with a wide choice of sandboxing and powering options by updating it frequently. This distro has been designed through containerization technologies like podman or doc to be compatible with most devices.
Features Parrot OS
- Parrot OS provides complete support for the .net/mono framework.
- It comes with custom Anti Forensic tools, GPG, and cryptsetup interfaces. Additionally, it provides support for encryption tools like VeraCrypt, LUKS, and Truecrypt.
- This operating system supports Anonsurf, Tor, I2P, and other anonymous networks.
- It is a lightweight operating system that provides anonymity for the internet.
8. Discreete Linux
Discreete Linux is an operating system whose primary purpose is to protect data from surveillance attacks with Trojan software more simply and accurately. The Discrete Linux project aims to protect against trade unions, journalists, defenders, political watchdogs, activists, etc. It creates an isolated and secure environment to encrypt/decrypt and process sensitive data. Users can easily use this operating system without high-security requirements.
Features Discreete Linux
- Discreete Linux prevents the user from network attacks.
- It is an immutable system.
- It supports the signed kernel modules.
- The user does not require any root privileges.
- This operating system provides a user-friendly interface and powerful options to hide the identity on the internet.
9. Alpine Linux
Alpine Linux is a general-purpose, non-commercial and free Linux distribution designed specifically for power users who appreciate resource efficiency, simplicity, and security. Alpine Linux is designed around the busy box and musl libc. Alpine Linux is more resource-efficient and smaller than traditional GNU/Linux distributions. In this, 130 MB storage is required for disk installation as well as installing a container does not require more than 8 MB. Alpine Linux provides a complete Linux environment and a wide selection of packages. The Alpine Linux init system uses OpenRC and compiles all user-space binaries to ensure stack-smashing protection.
Alpine makes use of apk-tools, a package-management system, and shell scripts. Alpine Linux is a run-from-RAM operating system. The Alpine Local Backup (LBU) tool allows all configuration files to be backed up, usually shortened to apical. These backup files are stored in the tar.gz file, which is a copy of all changed files by default.
Features of Alpine Linux
- The most commonly used packages in Alpine are Firefox, Xfce, and GNOME.
- An embedded environment with multiple directories can be reliably managed by adding additional directories.
- Every package is compiled to mitigate userland buffer overflows as part of stack-smashing protection.
- Alpine allows efficient network VPNs using the DMVPN standard that is included in its patch by default.
10. PureOS for Privacy
PureOS is one of the best Linux Distros when it comes to having a free OS for privacy. This operating system provides a platform where you can access the internet with complete privacy, security, and anonymity. Based on Debian it offers access to its huge community of developers who work hard to resolve the issues and bugs from the operating system.
Features of PureOS
- PureOS has a great accessibility option for the web.
- You can secure your data and files from multiple attacks.
- PureOS has KDE Plasma as a Desktop environment.
- The default search engine in PureBrowser is DuckDuckGo.
Wrapping Up
This article provides users, security researchers, software developers, and pen testers a selection of excellent uniquely secure Linux distros for their privacy and security, keeping an eye on online concerns.