Linux operating systems are popular among hackers because of open-source code, high customization, and the availability of lots of Linux hacking software, and all this without paying any money…
In one word, why the advanced users prefer to use Linux distro for hacking and penetration testing is the “Control“. As an infosec professional, hackers require the utmost control over their system while maintaining privacy which is not possible with Windows that is wholly owned and controlled by Microsoft or macOS by Apple. Linux offers unmatched customizability and a vast arsenal of tools one might consider to test electronic fortresses. Compared to Windows, Linux is much more secure owing to the publicly available code base and open source culture. Linux offers a multitude of different flavors (called distros). These customized distros come pre-bundled with the many tools that infosec professionals might require.
Why Linux is popular for hacking and penetration testing?
Well, there are a couple of reasons why advanced users prefer to go for Linux instead of Windows for hacking, and here are some…
1. Dedicated Linux Hacking Distros
Linux distros code is opensource thus, many developers or community offers a dedicated operating system with all tools and utilities required to accomplish hacking or for testing the security of application or network… Here are some top Linux distros for hacking…
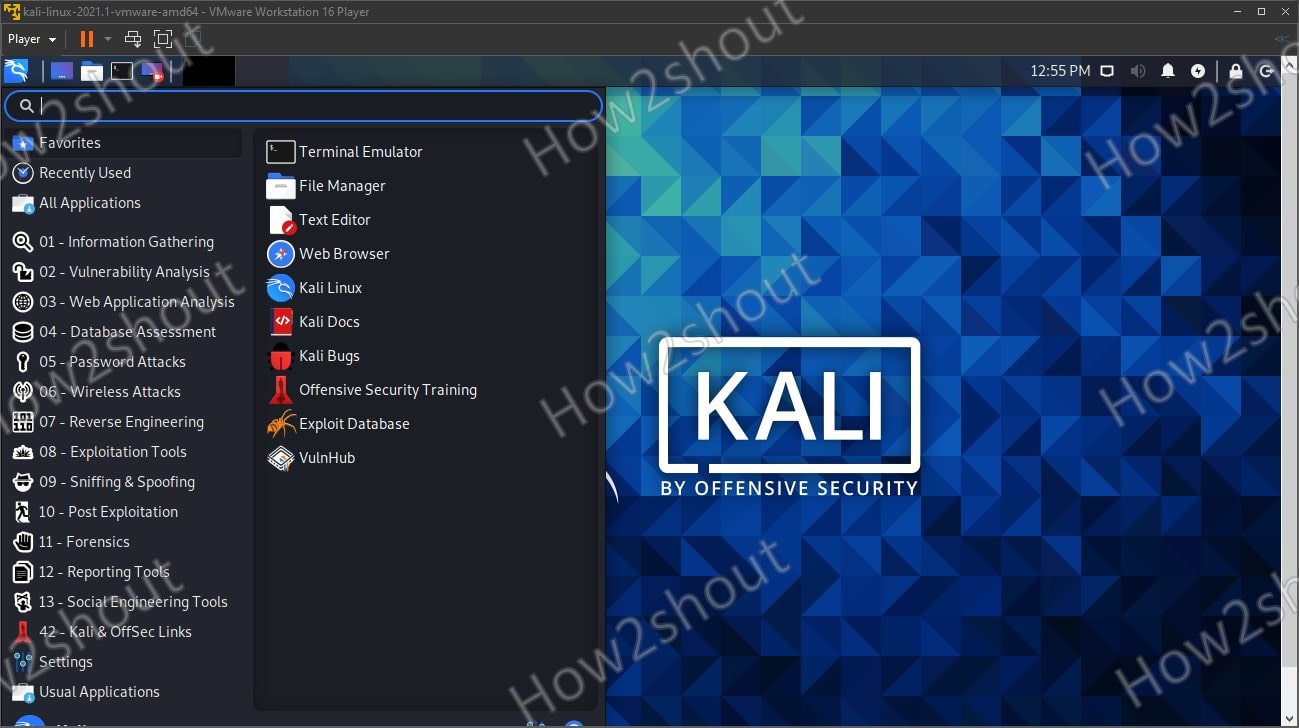
1. Kali Linux
By far the most popular “hacking”/penetration testing Linux OS out there. (Link: https://www.kali.org/). Kali has a vast dimension of tools pre-installed and one can get up and running in a very short amount of time. See: How to Download and install Kali Linux Vmware Image.
2. Parrot OS
Refined UI, lightweight and expert support are some of the USPs of this distro. (Link: https://parrotlinux.org/). Dedicated CDN’s mean lightning-fast downloads. Surfing the web privately has been made extremely easy on this OS.
3. BackBox
Based on Ubuntu, this OS consumes minimal resources and offers a simple and easy-to-use desktop manager (Link: https://www.backbox.org/). It has been specifically designed to reduce redundancies. Enables users to simulate attacks on applications or networks.
2. Linux offers a High-level customization
Linux also offers an extremely powerful and high-level CLI (command line interface). This terminal can be used to modify everything on the systems that you have access to.
Hackers also never want to move their hands to the mouse and then back to the keyboard. This wastes precious time. Linux offers several window managers that provide tiling options. One may open an ‘n’ number of terminals and programs which automatically get resized to fit the entire screen (we recommend i3 gaps). These window managers use keyboard shortcuts for navigation, opening programs, and resizing. This results in an extremely efficient workflow without having to move your hands.
Furthermore, if you won’t like the default Linux graphical user interface then switch to any other available such as Xfce, Cinnamon, Fluxbox, Gnome, Budgie, Deepin, etc… or create your own.
3. Availability of Hacking Tools
Hackers do not want to be tracked and having an open-source code base that can be looked at and modified by anyone to suit their needs is perfect. Of course, this is not offered by mainstream operating systems like Windows.
Linux has an extremely easy to use task scheduler called cron. One may set up cron jobs to run at intervals and perform tasks that would otherwise eat up valuable time. If it can’t be automated, break it down into simpler tasks.
Cron is just a small & common example, apart from it a wind range of tools available to support the hacking process such as password crackers, network, vulnerability scanners, network detectors, wireless packet sniffing, intrusion detection software, and more… All the major Linux distribution mention in this article such as Kali Linux, Parrot, and BlackBox come out of the box with such kind of tools for hacking and penetration testing thus, unlike Ubuntu and other common Linux desktop the user doesn’t need to waste his time in installing them one by one on some dedicated Linux distro meant to meet the demands of hacking/testing.
4. Live CDs & Less resource consumption
As compared to Windows, the Linux operating systems are less resource-consuming depending on what kind of desktop environment you are using, that is why we can easily use them in a Live environment. Almost all Linux distributions have a Live CD / USB option. Thus, we can run hacking tools on any system without actually installing our Linux OS.
5. Secure installation sources – easy update
Being a large community and open source code, anyone can see what is inside the Linux packages you are going to install on your system, thus reduces the chances of backdoors and malicious code. By default, Linux users obtain additional software exclusively from the secure package sources of their Linux distribution. Moreover, the Linux updates we will get most are not only reputable but also regressively tested programs because many clouds and hosting servers are using Linux as their main operating system. Another advantage of the package sources is the simple system update including all installed programs, which can be done with a command-line (apt-get dist-upgrade on Debian systems) or even fully automatically.
Moreover, if you are skeptical about any software binary, go ahead and compile that program from its source code. Furthermore, it is impossible under Linux that a malicious script is accidentally started from the Internet. The download cannot be executed until the user explicitly grants the file the executable bit with root rights, be it on the command line or in the graphical file manager. And that is now wholly true for Windows, any EXE file can be started from the darkest corners of the Internet if the program is satisfied with the user context. This gives hackers a secure place to start their bids…
6. Suitable for programmers
It supports almost all programming languages used such as C / C ++, Java, Python, and Ruby. In addition, it offers a wide variety of useful applications for development and scripting.
7. No need for Antivirus software
Linux users hardly need any antivirus program and that’s the reason why most Anti-virus companies only focus on Windows rather than Linux. Although with Windows 10 Defender you won’t any third-party software for now, however, that is another topic to discuss. This makes hackers rely more on Linux and with hardened ones, it becomes a highly secure environment to finish hacking and testing tasks.
Closing thoughts:
Summing things up, hackers want anonymity, intimate control, and above all, not having to deal with mouse pointer inaccuracies. Linux is the heaven-sent bundle that can be ordered to preferences. Also, did I mention it’s completely free? Breakaway from paying for proprietary software.
Other Articles:
- 5 Best free to use Linux Server distributions for 2021
- Popular Linux Distros for Beginners in 2021
- Top Linux Distros to use on Home PC or Laptop
- Whonix vs Tails Linux