Learn how to install and configure Ansible on Ubuntu 20.04 LTS Linux to automate administrator tasks for a group of servers from a single system.
If you have to manage multiple Linux servers then manually configuring and installing software on each of them is not only a time-consuming but also a labor-intensive task. Thus, Automation or orchestration is used in such environments.
Steps to install Ansible on Ubuntu 20.04 LTS
1. Update Ubuntu 20.04
Here we are using Ubuntu 20.04 to configure as an Ansible Node server or desktop, so go to its command terminal and first run the system update command where you are planning to set up Ansible. In the short run the given command in your Ubuntu 20.04 server.
sudo apt update3. Ansible PPA to install it on Ubuntu 20.04
The Ansible package is already present to install using the default system repository of Ubuntu 20.04. Therefore, simply run the given command using the APT package manager.
However, the version through the default repo is not the latest one, therefore here we are using the PPA repo of Ansible for the latest version of it.
sudo apt install software-properties-commonsudo add-apt-repository --yes --update ppa:ansible/ansiblesudo apt install ansibleAccept the request to install packages by typing – Y and hit
4. Check the Ansible version on Ubuntu 20.04
Let’s check the installer version of Ansible on our system using-
ansible --version5. Configure Host Servers
The servers which you want to manage using Ansible must have SSH installed and port 22 opened in the firewall to access them from other systems such as the one installed with Ansible.
For example, you have servers running on Ubuntu, Debian, and CentOS that you want to manage and configure using Ansible. Thus, we need to install the SSH server and open port 22 on them, you can use these commands.
For Ubuntu & Debian servers-
sudo apt install openssh-server
sudo systemctl enable sshto allow port 22 in the firewall-
sudo ufw allow 22For RHEL or CentOS
sudo dnf install openssh-server
sudo systemctl enable sshdAllow 22 in firewall-
sudo firewall-cmd --zone=public --permanent --add-port=22/tcpSo, here to perform this tutorial we have three servers Ubuntu, Debian, and CentOS, here are the IP addresses in our case.
Ubuntu – 192.168.189.172
CentOS – 192.168.0.102
Debian – 192.168.0.104
6. Generate SSH Keys on Ubuntu 20.04
To install packages or perform some deployment on a remote target server, create a pair of SSH keys on localhost (control node) and then push them on each remote server so that we can manage them using SSH.
Simply type and hit the Enter key multiple times until the generation of keys is not done.-
ssh-keygen7. Copy SSH keys to Remote or host servers
Now, push the generated key on Ubuntu 20.04 Linux to the remote servers that you want to configure or manage. You should know the user name of the remote server or use the default root user.
Note: Replace h2s with remote servers’ sudo users or use the default root. Also, replace the Ip-address with your server’s.
Example:
ssh-copy-id [email protected]
ssh-copy-id [email protected]
ssh-copy-id [email protected]Now, on each server run the below command, so that we can run commands with sudo on them using Ansible but without entering a password.
echo "$(whoami) ALL=(ALL) NOPASSWD:ALL" | sudo tee /etc/sudoers.d/$(whoami)If we don’t run the above command then while running Ansible to manage the remote server, we would get the following error:
192.168.xx.xx | FAILED | rc=-1 >>
Missing sudo password8. Create Inventory File for Remote Hosts
In Ansible, we create a file where we will define all the remote hosts or target systems that we want to manage. We can also create a group of hosts, for example, one group is a Web server that only contains a remote system running some web servers such as Apache, and the other can be a group of Mysql running a database server and so on. The Inventory file is also important because using it the command, modules, and tasks in a playbook will operate.
So, as here in this tutorial we have three remote servers, let’s add them to the Ansible host file.
sudo apt install nano -ysudo nano /etc/ansible/hosts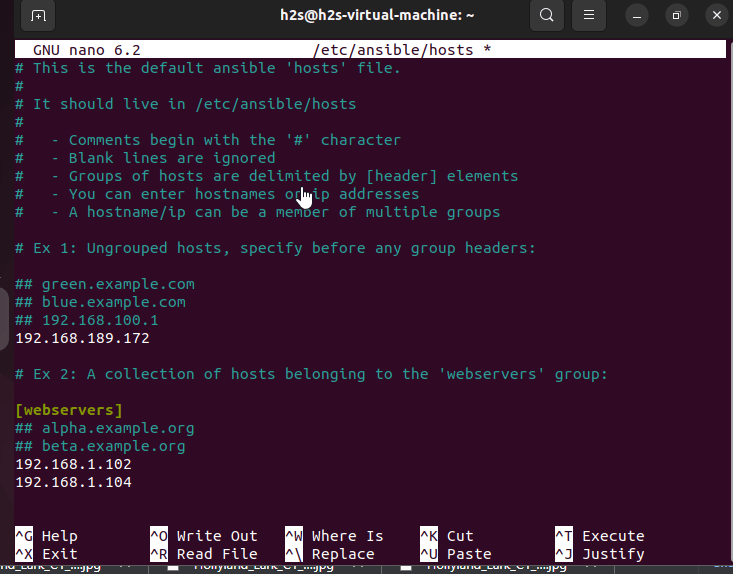
If you don’t want to create any group then simply paste your remote server Ip-address or domain name there in the file, whereas for creating a group you have to specify that before adding Ip-addresses. You can edit the default Ansible inventory file values that would already have some examples or add your own at the end of the file.
Here I am adding two servers for a host group identified by webservers and one server will define as an individual.
In the following screenshot, you will see-
192.168.189.172It is an ungroup server
whereas
[webservers]
192.168.0.102
192.168.0.104are in a group called webservers. The benefit of creating a group is, we can issue one command to a whole set of servers defined in that particular group of hosts. For example, I can install an apache server on all remote servers added in a group called webservers simultaneously. In the same way, you can define database groups and others.
Note- Inventory with custom SSH port
If you are using some server not with the default 22 SSH port, for example, a server running on Docker then we can also define that with the Ip-address. Example-
192.168.0.104 ansible_user=remote-server-username ansible_port=49153⇒ In the above command replace the IP address, remote-server-username, and port number and add it to the inventory file.
To save the file just press Ctrl+X, Type-Y, and hit the Enter key.
9. Ping All added Remote servers
As we have created the inventory file successfully, let’s check whether our Ansible could ping all the added servers or not, for that-
To ping a group of hosts-
ansible -m ping group-nameexample– ansible -m ping web-servers
To ping a single server
ansible -m ping ip-addressexample– ansible -m ping 192.168.189.172
To ping all.
ansible -m ping allExample for Output:
192.168.189.172 | SUCCESS => {
"ansible_facts": {
"discovered_interpreter_python": "/usr/bin/python3"
},
"changed": false,
"ping": "pong"
}To check for a particular user, we can run
ansible all -m ping -u your-remote-server-userNote: Replace “your-remote-server-user” with the user you want to check.
10. Ansible commands
Now, let’s say you want to install an Apache web server on one group of servers you have defined in the Inventory file. As here we already named one webserver, thus we use that, you can use whatever name you have given to your group of servers.
Command syntax
ansible -b --become-method=sudo -m shell -a 'command to execute' webservers
For example, running the update and installing the apache server on remote Debian and Ubuntu systems simultaneously.
ansible -b --become-method=sudo -m shell -a 'apt update' webserversInstalling Apache
ansible -b --become-method=sudo -m shell -a 'apt install -y apache2' webservers
To run the same above command for all defined remote PCs run-
ansible -b --become-method=sudo -m shell -a 'apt install -y apache2 ' allFor ungroup hosts, you can use their IP addresses, for example-
ansible -b --become-method=sudo -m shell -a 'apt install -y apache2' 192.168.0.104You can also use other commands that don’t require sudo such as for checking uptime-
ansible -m command -a "uptime" group-name/ip-adress The same above command can be used for other purposes, just replace uptime with the command that you want to execute on a remote server and also change the group name/IP address.
For more information refer to the official Documentation